Advanced traffic analytics using Fusion's SD-WAN
📈 Elevate Your Network Game with Fusion's Advanced Traffic Analytics (ATA) 🚀 In the world of SD-WAN, traffic analytics is the secret sauce that unlocks a realm of possibilities. 💡 It's the key to understanding your last mile, fortifying your network's security, and gaining unparalleled insights into data usage. 🌐 Enter Fusion Broadband South Africa's Illuminate platform – your ultimate ATA sidekick! 💥
Traffic analytics is an important component of SD-WAN. It provides an ability to have visibility to the usage of a last mile, as well as additional such as information security insights. Fusion Broadband provides advanced traffic analytics (ATA) using the Illuminate platform. This is in addition to the current network performance management abilities as well as the ability to directly use wireshark from your laptop to capture packets remotely off the edge hardware.
Besides last mile outages and the causation associated around the problems related to these, the next item that always comes up at a site is who or what is using the bandwidth. Fusion is easily able to answer this using its advanced traffic analytics by providing full transparency to network activity for a site owner. These capabilities exceed those provided by most firewall vendors!
Deployment scenarios
The solution can be deployed in two ways:
directly on the SD-WAN edge where the device is configured to be used as a broadband router. This implies that it does the upstream connectivity to the ISPs using either PPPoE, DHCP, or statics. Also the edge provides the NAT layer as well as performs rudimentary port forwarding if required.
using a switch port mirror when a 3rd party firewall is used at the edge behind the SD-WAN device. The switch port mirror is configured to mirror the internal default gateway of the firewall.
The deployment of the agent to the SD-WAN device is implemented using Fusion's leading automation abilities. Its as easy as pie. Not only does Fusion make any firewall more reliable with managing multi-links it provides better metrics as well.
Lightweight edge agent
The solutions using a lightweight agent on the edge which streams telemetry to a cloud portal. The use of compute and network resources on the edge is negligible, especially when compared to some resource hungry alternatives such as netflow/IPFIX which are debilitating slow especially and higher bandwidth speeds approaching gigabit speeds. The ATA architecture of Fusion is a dramatic step up from legacy traffic visualization mechanisms and is significantly more cost effective.
The Fusion standard SD-WAN offering is shipped with a 48 hour trend and statistics ability while a longer term monthly and yearly archive attracts an additional service charge. The ATA ability of Fusion's SD-WAN make it a viable deployment for both single and mult-link last mile installations. In actual fact, deploying Fusion's SD-WAN is the most cost effective traffic visualization solution on the market! And to top it all, its is better than many of those extremely expensive tools.
Inventory
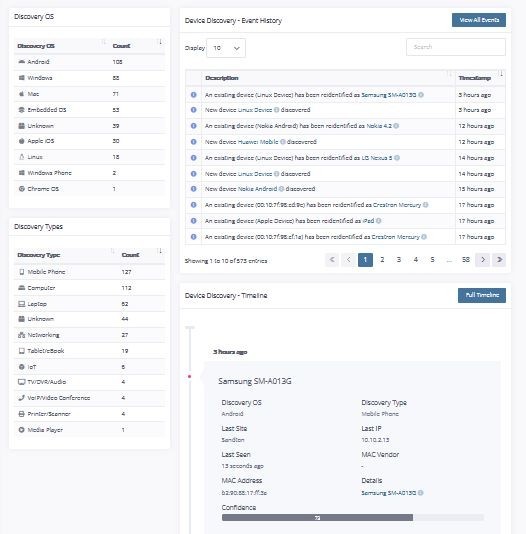
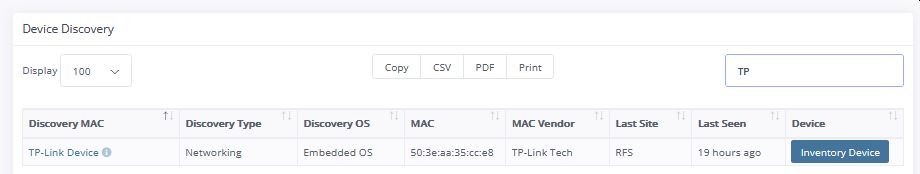
One of the first abilities highlighted by a deployment of ATA is inventory. All devices at a location are detected and identified. In a typical location a user now would have a laptop, mobile phone and watch. Additional devices are cameras, printers, wireless access points, televisions and VoIP phones. In many cases IoT devices are also deployed such a roombas. ATA creates a usable inventory of all of these and provides the ability to selectively spotlight any of them.
As an example, an organization may have a particular policy stating users at a particular site are not permitted to engage in certain activities. Often the is related to employees not being permitted to view porn. Adult education centres might also not allow bittorrent downloads or crypto-mining. ATA is ability to provide visibility to all these transgressions and record them. The ATA logs are then used and submitted in any disciplinary actions.
The inventory is able to publish an extensive list of device attributes including vendor, category, IP and MAC address, as well as times discovered and last seen.
In some cases users might deploy unauthorized wireless access points that will interfere with the sites own access points. These are quickly identified,
Applications
Fusion's ATA has a best in class deep packet inspection (DPI). It is thus able to identify the significant majority of applications in use. It provides graphs and reports on these sorted from highest to lowest bandwidth use as well as dividing the use into upload and download. It quickly identifies bandwidth hogs.
Name resolution
An extensive and comprehensive name resolution report exists for a site. This provides the ability to have detailed reporting on Internet usage at a site. Besides identifying each and every site to which users connect, the reports categorize connection so it is possible to see the breakdown between business use and social media use as an example.
The abilities extend to being able to identify to which countries the most connections are being established.
Malware
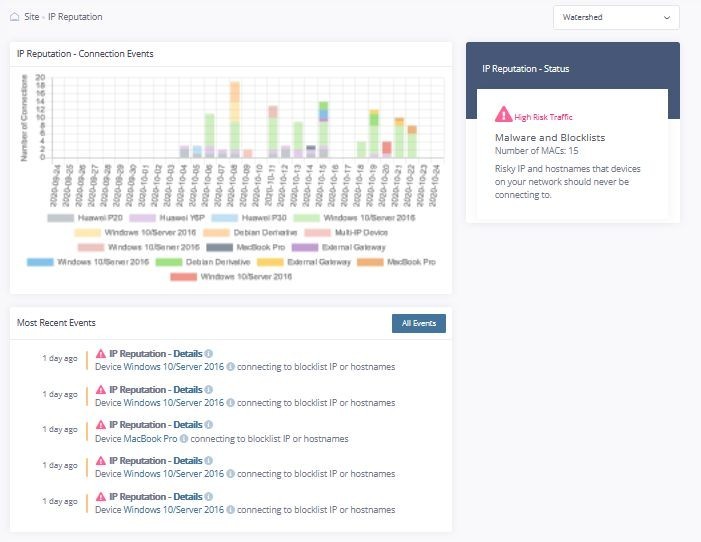
ATA identifies malware by being out of band to the user device. Sophisticated malware often disables the information security agent of the laptop of a user and these are in most cases these are not detected and lurk for months, even years, under the radar at a site. Fusion is able to immediately detect these sneaky applications and report on them. It is also able to report on IoT devices that have been compromised as often these do not event have information security agents.
This ability of ATA makes it a crucial mitigation in preventing future ransomware attacks as a site owner will have a heads up to it going down well before it is triggered. It would be able to mitigate a situation as what recently happened at the Department of Justice in South Africa which was severely impacted by a ransomware attack.
Any access to known command and control servers for botnets are logged and immediately visible.
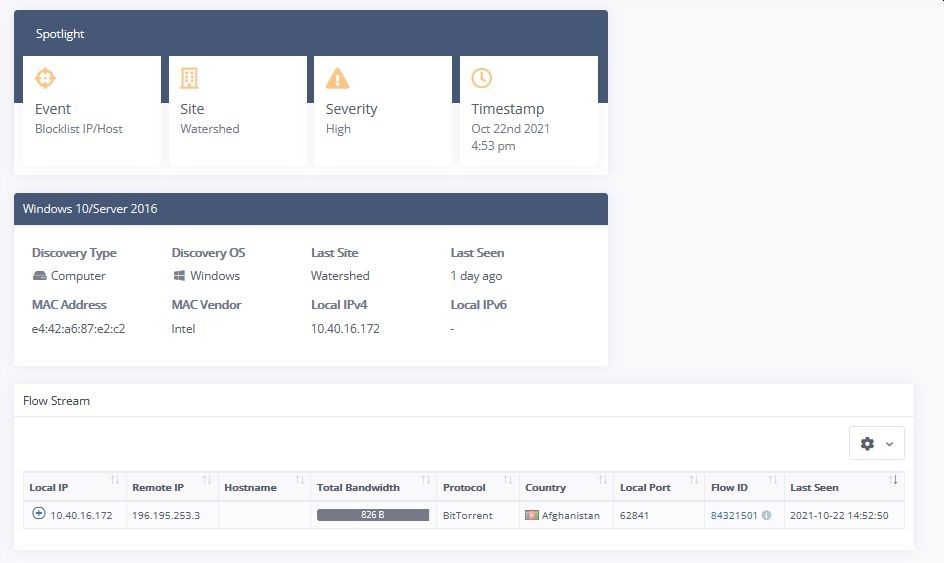
The IP address can be pasted into IBM X-Force to obtain more details. Here is an example of one that was detected with high risk!
Data leak protection
Many IoT devices, operating systems and even browsers have a call home facility. As an example you might have a camera manufacturer that is leaking information back to a jurisdiction to which you do not have knowledge. ATA identifies these breaches allowing site owners to mitigate their risks.
Network level protection
Fusion's ATA identifies the DHCP and DNS servers being used at a site. A site owner is thus able to identify rogue DHCP services which would disrupt connectivity at a site. It will also be able to identify unauthorized DNS servers being used in man in the middle attacks. A site owner can also audit the use of file servers. All file servers are identified included ones that use the legacy version 1 protocol that is a popular target used to propagate ransomware. Many organizations are still in whack a mole mode with a known ransomware variant known a wannacry due to these legacy systems.
Fusion's ATA is also have to identify and highlight which users are accessing the dark web.
The ability to provide visibility into network level-protection also extends to identify encrypted connections and those connections using dated and insecure protocols that are easily compromised.
Identification of local services
All local web services (HTTP/S) and remote desktop protocol (RDP) servers are identified allowing the site owner the ability to determine if the deployment of these are authorized and valid. Fusion's ATA also identifies all the different types of VPNs being used at a site.
The ATA's ability even extends to being able to identify the use of 3rd party SD-WAN appliances at a site.
To install Illuminate on an edge use:
salt-call state.sls illuminate-t
Author
Ronald Bartels provides solutions to networking and last mile reliability problems. The solution from Fusion Broadband allows a business to stay 100% connected, avoid downtime and keep working. The Fusion Broadband solution has been installed in many vertical industries including state owned and private entities. In addition to the IBM Beacon Award 2020 for Infrastructure Services, the solution is a mature software platform that has over 2000 installed instances of multiple site private wide area networking deployments.
Ronald is dedicated to connecting Internet-inhabiting things at Fusion Broadband, where connectivity excellence is the ultimate goal.
The Unbundled podcast:
🔮 Embark on an exhilarating journey through South Africa's complex fibre landscape!
🌐 Join the conversation with SD-WAN experts Ronald Bartels & Kirthesh Sundersingh from Fusion Broadband South Africa.
🎙️ Unveil the game-changing power of SD-WAN, exclusively on CliffCentral's Unbundled podcast hosted by Jaco Voigt.
🚀 Don't miss this thrilling exploration of connectivity's future! 🌟 Listen now!
#ConnectivityUnleashed #PodcastDiscovery
Interview with Arthur Goldstruck
📺 Tune in to this captivating interview on eNCA featuring Arthur Goldstuck, as he delves into the game-changing power of Fusion Broadband South Africa's SD-WAN! Discover how it can effortlessly tackle load shedding and connectivity issues over broadband links from Afrihost and Comsol Networks. Don't miss out on the must-have solution for businesses in South Africa! 🇿🇦🌐
#LoadSheddingSolved #SDWAN #BusinessSolutions #SouthAfrica #FusionBroadband
Contact Fusion
Experience uninterrupted connectivity with Fusion Broadband South Africa's SD-WAN! 🌐 Say goodbye to downtime and connection issues. Fusion makes it affordable & easy for businesses to stop downtime by fusing multiple connection types from different ISPs together. It's so seamless, you'll never notice when a connection has failed. No more frustrating reconnecting, refreshing, or redialing!
At Fusion Broadband, we specialize in connecting the Internet of Things (IoT) and offer solutions designed to keep your connectivity failure-proof Learn more: Link to contact Fusion about their SD-WAN Solution! 💼🚀
#SDWAN #Connectivity #BusinessContinuity